Other public cloud services (incl. Platform as a Service (PaaS)) cost as a percentage of total IT cost, excluding depreciation/amortization
This measure calculates cost of other public cloud services (other than SaaS or IaaS) including Platform-as-a-Service (PaaS) as a percentage of the total IT cost. Software as a Service (SaaS) is model for distributing software in which a service provider hosts applications and makes them available to customers over the internet. Infrastructure as a Service (IaaS) describes cloud computing that permits allocation, computation, networking, storage and security resources on demand. Total IT Cost or Budget (excluding depreciation/amortization; i.e., based on cash flow) includes operating and capital expenses for performing the entire IT function. Operating expenses are independent of including or excluding depreciation/amortization. Capital expenses should include costs for all capitalized IT assets acquired during the reporting period. The Function "manage information technology (IT)" (20607) includes [Managing process groups relevant to the business of information technology within an organization. The process groups include "Develop and manage IT customer relationships", "Develop and manage IT business strategy", " Develop and manage IT resilience and risk", " Manage information", " Develop and manage services/solutions", "Deploy services/solutions", and " Create and manage support services/solutions".]. This Cost Effectiveness measure is intended to help companies understand this cost expenditure related to the process group "Manage IT resilience and risk".
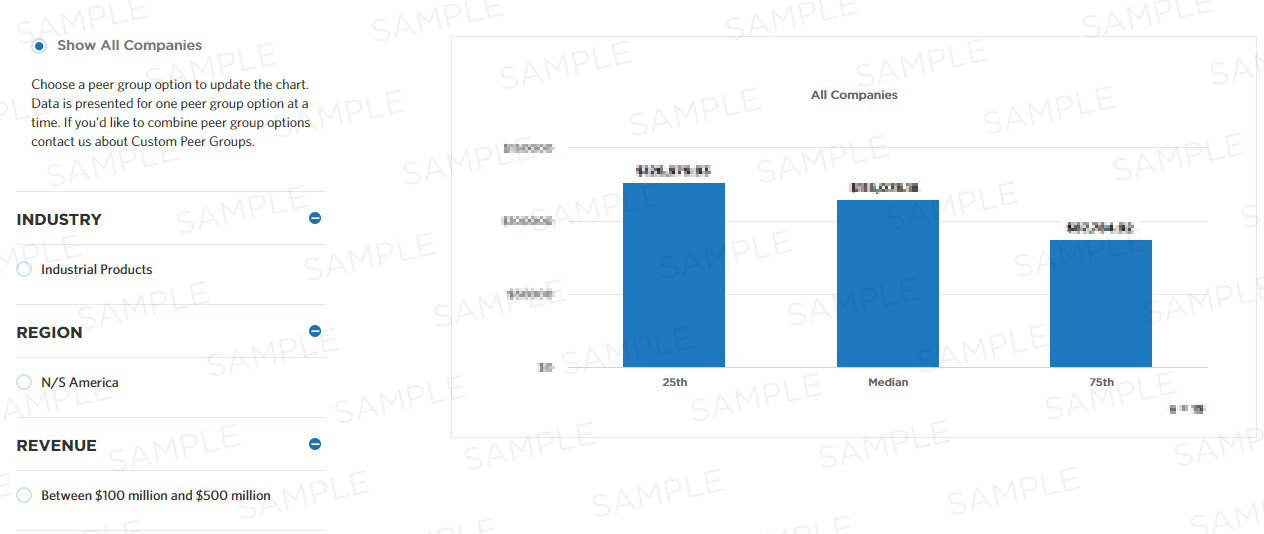
Benchmark Data
| 25th | Median | 75th |
|---|---|---|
| - | - | - |
Compute this Measure
Units for this measure are percent.
Other public cloud services cost as a percentage of total IT cost, excluding depreciation/amortization