Internal personnel cost, including benefits, as a percentage of total IT cost, excluding depreciation/amortization
This measure calculates the cost of internal personnel (including benefits) as a percentage of the total IT cost. Personnel cost refers to employee personnel compensation (salaries and wages, bonuses, overtime and benefits) and fringe benefits (e.g. contributions made towards agovernment retirement fund for employees, workers compensation, insurance plans, savings plans, pension funds/retirement plans, stock purchase plans), and special allowances such as relocation expenses and car allowances. Total IT Cost or Budget (excluding depreciation/amortization; i.e., based on cash flow) includes operating and capital expenses for performing the entire IT function. Operating expenses are independent of including or excluding depreciation/amortization. Capital expenses should include costs for all capitalized IT assets acquired during the reporting period. The Function "manage information technology (IT)" (20607) includes [Managing process groups relevant to the business of information technology within an organization. The process groups include "Develop and manage IT customer relationships", "Develop and manage IT business strategy", " Develop and manage IT resilience and risk", " Manage information", " Develop and manage services/solutions", "Deploy services/solutions", and " Create and manage support services/solutions".]. This Cost Effectiveness measure is intended to help companies understand this cost expenditure related to the process group "Manage IT resilience and risk".
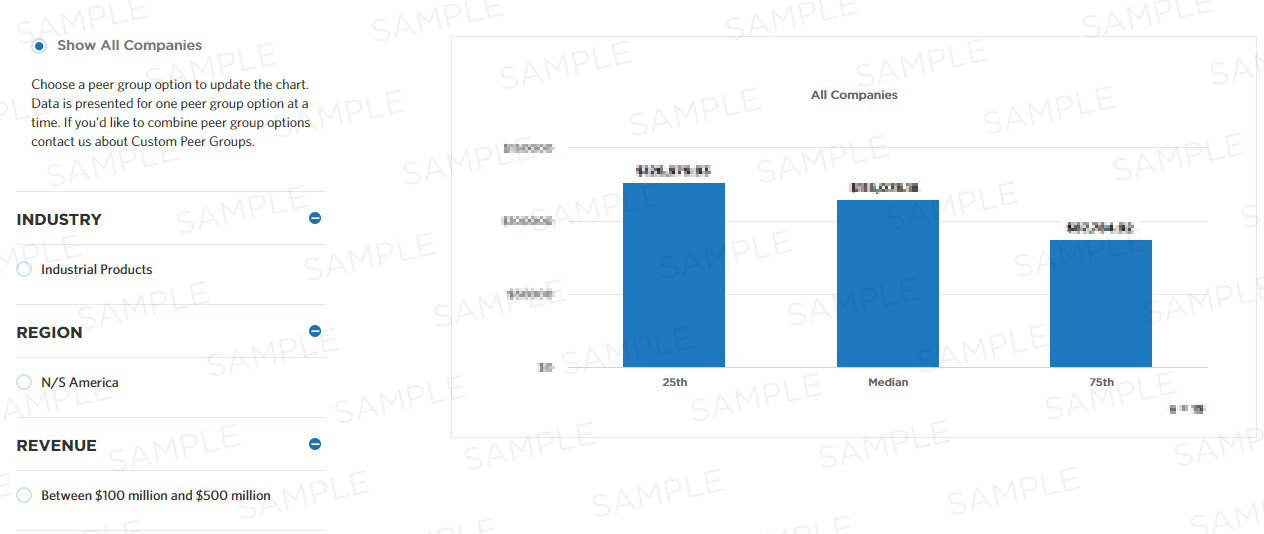
Benchmark Data
| 25th | Median | 75th |
|---|---|---|
| - | - | - |
Compute this Measure
Units for this measure are percent.
Internal personnel cost as a percentage of total IT cost, excluding depreciation/amortization